Stellenbosch Remote Work: Keep Your Devices Secure & POPIA-Compliant
Remote work in Stellenbosch: quick device hardening, smart backups, and POPIA-safe disposal with CoDD—plus fast remote help when something breaks.
· Digissential Team · 4 min read
remote work security stellenboschpopia laptop support stellenboschremote it supportprivacybackup
TL;DR: For Stellenbosch home offices and Technopark teams: encrypt your laptop, turn on MFA, keep versioned backups, and retire devices with a Certified Wipe (CoDD). If anything feels off, start a Remote IT Support session—fast, local, and POPIA-aware.
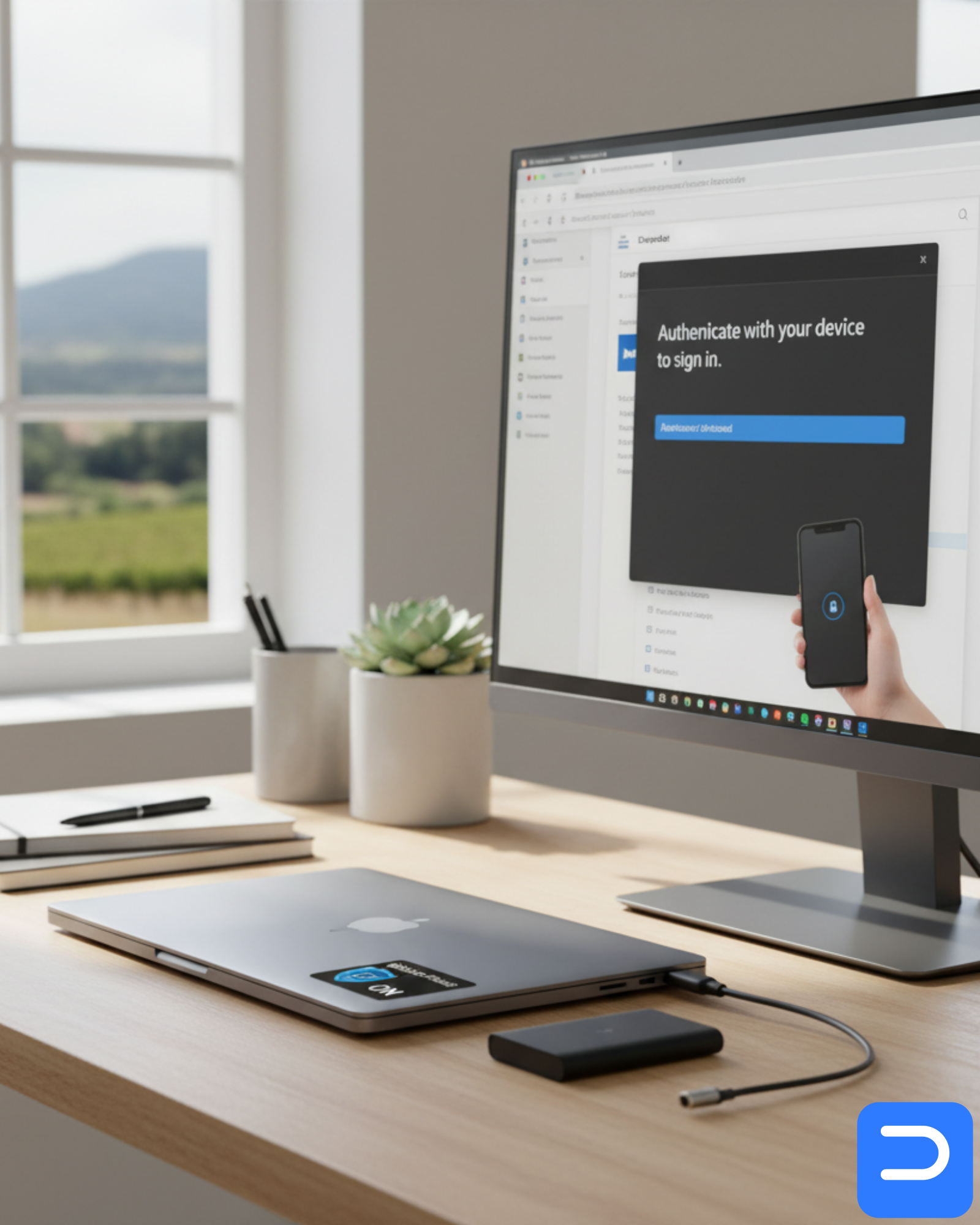
Working from Stellenbosch homes and Technopark offices means client data often lives on a single laptop. That’s convenient—and risky. A lost bag, a bad attachment, or a quick resale of “old” hardware can become a POPIA headache. This guide shows practical steps that don’t slow you down: quick hardening, restore-tested backups, and a clean exit plan with CoDD certificates when devices retire.
What you’ll learn (quick wins)
- A 20-minute hardening routine that meets day-to-day POPIA expectations.
- How to back up right (cloud + external) and prove it with a restore test.
- When to get remote help and how we keep sessions privacy-first.
- Why a Certified Wipe (CoDD) closes your compliance loop at end-of-life.
Identify the risks (you’ll recognise these)
- Lost/stolen laptop with unencrypted storage.
- Phishing or MFA fatigue prompts on personal email that also accesses client files.
- Sync mistakes: deleting a folder removes it everywhere.
- Shadow IT: personal USB drives with sensitive exports and no audit trail.
- “Factory reset” handed to a buyer—data still recoverable without a verified wipe.
Safe steps (do this in order)
-
Encrypt the drive
- Windows BitLocker or macOS FileVault. Print or store the recovery key outside the laptop (password manager or secure file).
- For shared families/housemates, ensure only your user can unlock the device.
-
Lock down access
- Turn on MFA for email, cloud storage, and finance tools.
- Set auto-lock (5–10 minutes), and disable login via weak PINs on shared desktops.
-
Update + de-bloat
- Run OS/browser/driver updates. Remove unknown browser extensions and “optimiser” apps that inject ads or steal tokens.
-
Back up with a restore test
- Map Desktop/Documents to OneDrive/Google Drive and mark key folders Available offline.
- Plug an external SSD/HDD weekly for a second copy.
- Test: recover a dummy file from cloud and from the external copy. No test = no backup.
-
Harden the browser
- Block third-party cookies; enable Safe Browsing/SmartScreen; keep a separate Work profile with minimal extensions.
-
Prepare support
- Install our Remote IT Support tool in minimal-access mode. We start view-only; you escalate to control when needed.
- Save our support shortcut so help is one click away during deadlines.
-
Plan end-of-life now
- When it’s time to sell or recycle, use Data Destruction (Certified Wipe). You’ll get a CoDD listing device IDs, method, verifier, and date/time—your audit trail.
These steps mirror the HowTo block above, keeping your schema accurate and helpful.
Do-nots (costly mistakes)
- Don’t rely on delete/factory reset as a data-wipe—use a verified wipe with a CoDD.
- Don’t keep client data on the Desktop with no backup or version history.
- Don’t install random “PDF printers/VPNs” that hijack traffic; use reputable tools.
- Don’t accept remote control prompts you didn’t request—call us to verify first.
Time & support expectations in Stellenbosch
- Same-day remote hardening: we can secure settings, clean extensions, enable encryption (where supported), and verify your backup flow—without you leaving the desk.
- On-device issues: if hardware is failing or encryption won’t complete, we’ll advise an in-shop slot.
- Retiring devices: drop-off or collection can be scheduled; we’ll recover what you need, then certify the wipe (CoDD).
When to call us (skip the stress)
- You’ve spotted a suspicious login or MFA prompt you didn’t trigger.
- Files disappeared after a sync mistake—need version recovery.
- Laptop was lost/stolen—you need advice on account locks and device wipe status.
- You’re handing laptops to buyers or recyclers and need a CoDD for your records.
Book help (fast)
FAQs
Q: Should I use a VPN at home?
A: A VPN isn’t a silver bullet. Prioritise encryption, MFA, updates, and backups first. Use a reputable VPN when you’re on unknown networks or need to reach private office resources.
Q: My laptop is personal but used for work—okay for POPIA?
A: Yes, if you encrypt, use MFA, and keep separate profiles with backups. At retirement, request a CoDD to document the wipe before resale.
Q: Can you help us set up shared family devices safely?
A: Absolutely—standard (non-admin) accounts for kids/housemates, separate profiles, and POPIA-aware access rules so work data stays private.
Q: We run a small team—can you provide policies too?
A: We can supply light, practical checklists for remote work (encryption, MFA, backup cadence, CoDD on disposal) and tune them to your tools.
Compliance & trust
Updated on 2025-09-22.
